Caddo Parish (caddo.gov) Web Servers Compromised

Date: June 27, 2025
Summary:
Multiple subdirectories on the official web servers for the Parish of Caddo, Louisiana (caddo.gov) are serving or linking to explicit pornography, pirated movie content, and scam-related material (e.g., fake Roblox gift cards). These files are publicly accessible and indexed by search engines under the .gov domain. This indicates a likely web server compromise or unauthorized file upload vulnerability.
Contact:
Authorities were contacted but were not interested. After several attempts to contact someone at the Caddo.gov government I had to withdraw from contact due to time limitations. The FBI in New Orleans were also not interested, talked over me and essentially hung up on me.
Method of Discovery:
The following Google search was used to locate the files:
site:caddo.gov "roblox"
site:caddo.gov "movies"
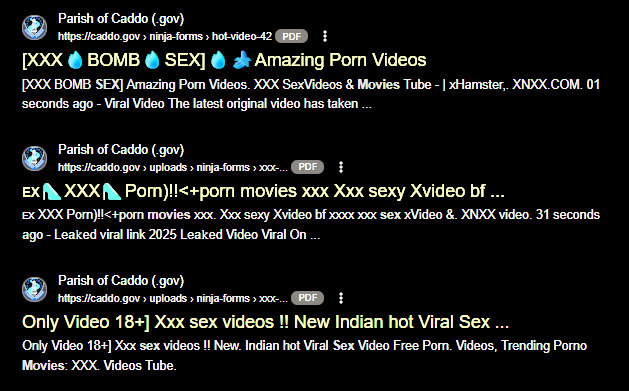
This search returned multiple PDF documents hosted on caddo.gov that include text referencing “Robux”, Roblox gift cards, sex exploitation material, movies and other scam-related content. Further manual browsing revealed additional PDFs promoting pornography and pirated media.
Examples of Affected URLs:
(Clicking these links may lead to explicit or malicious content)
https://caddo.gov/uploads/ninja-forms/xdfvds
Title: New special# How to Redeem Free Roblox Gift Card…https://caddo.gov/uploads/ninja-forms/ertss
Title: ++10000 FREE Robux-Generator Best Roblox Gift Card…https://caddo.gov/uploads/ninja-forms/hot-video-19
Title: XXX🔥Porn💋Amadora Porn Videos XXX Sex Videos…https://caddo.gov/media-streams-92162
Title: Free Porn Videos & XXX Movies: Sex Videos Tube…https://caddo.gov/uploads/media-stream-us-137
Title: WATCH^full—K.O. 2025 [!!FULLMOVIE!!] Available Now…
Technical Indicators:
- Many of the URLs follow a pattern using directories such as:
/uploads/ninja-forms//media-streams//uploads/media-stream-us-*
- Content appears to be uploaded as PDF files but contains spammy, explicit, or scam text and outbound links.
- The structure of these directories and filenames suggests possible abuse of third-party webform or file upload plugins (e.g., Ninja Forms).
Potential Vectors of Compromise:
- Unsecured or outdated third-party plugins (such as Ninja Forms) used for form handling or file uploads.
- Misconfigured file upload permissions allowing public access or listing.
- Absence of validation for file type or content during upload.
- Lack of access control on directories storing user-submitted content.
Risks and Concerns:
- Hosting of pornographic and pirated content on a
.govdomain undermines public trust. - Exposure of citizens to phishing, malware, and scam campaigns via embedded links.
- Possible unauthorized access to broader systems or databases.
- Violation of federal guidelines for
.govdomain usage and cybersecurity standards.
Recommended Actions:
- Immediate containment: remove all unauthorized files and disable public access to upload directories.
- Conduct a forensic audit of server logs and plugin activity to determine the attack vector and scope of breach.
- Notify the Cybersecurity and Infrastructure Security Agency (CISA) and appropriate federal authorities.
- Patch and secure any outdated plugins or server components.
- Notify the public if any user data may have been exposed.

