Mississippi Dept Finance Website Compromised.

Summary:
The official website of the Mississippi Department of Finance and Administration (dfa.ms.gov) appears to have been compromised. A variety of malicious and inappropriate PDF files—unrelated to the agency’s function—are being hosted on the site.
These files include scam-related content (e.g., free Robux generators), pornographic material, and pirated movie references. The presence of this content on a government-managed .gov domain poses serious security, reputational, and legal risks, and indicates a likely unauthorized breach or exploitation of the server.
About:
The Mississippi Department of Finance and Administration (DFA) is a state government agency responsible for the financial management of Mississippi’s resources, including budgeting, procurement, and personnel services. Its domain, dfa.ms.gov, is a trusted government address that carries an implicit assurance of legitimacy and security.
Method of Discovery:
The issue was discovered using a targeted Google search with the following query:
site:dfa.ms.gov "roblox"
site:dfa.ms.gov "movies"
This revealed dozens of PDF documents hosted on the site that advertise scams, inappropriate content, and illegal services. A manual inspection confirmed the presence of suspicious file names, irrelevant content, and non-governmental material—strong indicators of a breach. Additional exploration of directories such as /files/, /webform/, and /_sid_/ uncovered more evidence of inappropriate use and abuse of server resources.
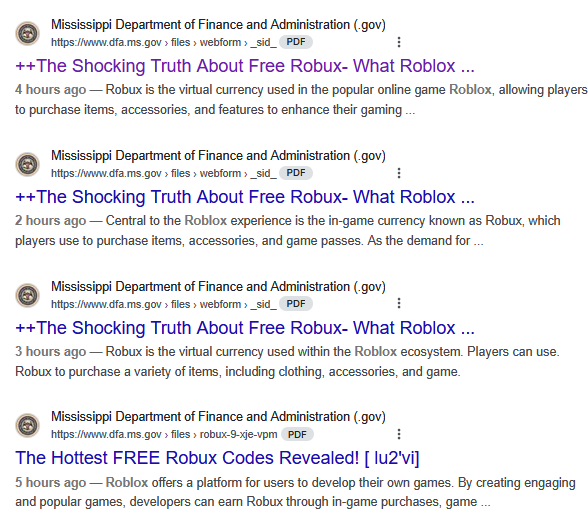
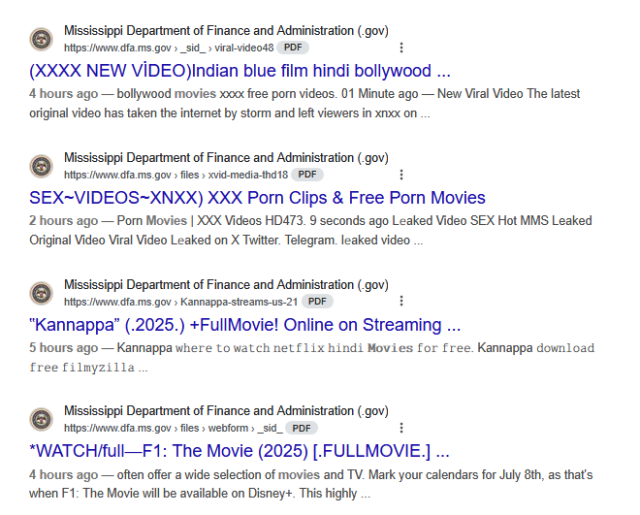
Examples of Affected URLs:
All URLs below point to PDFs hosted on https://www.dfa.ms.gov
/files/webform/_sid_/:- “The Shocking Truth About Free Robux”
- “Tap Into the Best Free Robux Generator Today”
- “Score Big in Roblox – Top 10 FREE Robux Codes”
/_sid_/viral-video48:- “Indian blue film hindi bollywood …”
/files/xvid-media-thd18:- “SEX
VIDEOSXNXX) XXX Porn Clips & Free Porn Movies”
- “SEX
/Kannappa-streams-us-21:- “Kannappa (2025) FullMovie!”
/files/webform/_sid_/:- “WATCH/full—F1: The Movie (2025)”
- “LILO & STITCH (2025) [.FULLMOVIE.]”
These examples illustrate clear abuse of the domain to host and distribute inappropriate or malicious material.
Technical Indicators:
- Numerous PDFs containing non-governmental content, including scams and adult material
- Common directory usage:
/files/,/webform/, and/_sid_/ - Repeated use of keywords such as “Robux,” “porn,” “stream,” and “full movie”
- Filenames and titles matching patterns often used in spam, phishing, and SEO manipulation
- Recently indexed content (hours ago), indicating active use of the compromised upload or file storage feature
Potential Vectors of Compromise:
- Unsecured file upload functionality (e.g., contact forms or user-submitted document portals)
- Exploitation of outdated CMS or web platform components
- Insecure server-side permissions allowing unauthorized file placement
- Compromised administrator or FTP credentials
- Lack of Web Application Firewall (WAF) or insufficient monitoring and intrusion detection
Risks and Concerns:
- Potential delivery of ransomware, malware, or phishing payloads via PDF
- User download of malicious files under the trusted
.govdomain - Exposure to credential theft or session hijacking through phishing content
- Public Trust: The presence of malicious or explicit content on a
.govdomain erodes public confidence in government-managed digital infrastructure. - User Safety: Visitors to the site could inadvertently download malware, fall victim to scams, or be exposed to inappropriate material.
- Legal Liability: Hosting such content may put the agency at risk of violating state or federal cybersecurity and content standards.
- Abuse of Infrastructure: The site may be exploited to distribute spam or as part of broader cybercriminal campaigns.
- Search Engine Reputation: Harmful files being indexed by search engines under a
.govdomain may mislead users and damage the state’s digital reputation.
Recommended Actions:
- Immediately isolate and remove all unauthorized files and directories.
- Initiate a comprehensive incident response process, including forensic analysis of logs, user access, and server behavior.
- Audit and disable any public-facing upload features until fully secured.
- Reset all administrative and server access credentials and implement multi-factor authentication (MFA) across all accounts.
- Perform a full malware scan of the server and check for persistent backdoors or scripts.
- Apply all pending security patches to CMS platforms, plugins, and underlying software.
- Implement a Web Application Firewall (WAF) and activate intrusion detection systems.
- Notify relevant agencies, including:
- FBI Internet Crime Complaint Center (IC3) – https://www.ic3.gov
- Cybersecurity and Infrastructure Security Agency (CISA) – https://www.cisa.gov
- MS-ISAC (Multi-State Information Sharing & Analysis Center) – https://www.cisecurity.org/ms-isac
- Temporarily remove the affected site or affected subdirectories from public access until integrity is restored.
- Request de-indexing of compromised URLs from Google and other search engines to reduce user exposure.


