DEA.GOV Web Server Compromised.

Date:
June 27, 2025
Summary:
A section of the DEA’s official web presence—specifically the DEA Museum site (museum.dea.gov)—has been compromised. Numerous PDFs and page listings are publicly accessible that include sexually explicit content, pirated media advertisements, and scam-related topics such as Roblox Robux giveaways. These are being served from within .gov infrastructure, including from directories associated with file uploads and forms. This breach suggests that attackers were able to inject or upload unauthorized files through vulnerable input vectors.
Contact:
Initial contact with the DEA indicated they did not believe their web server or web sites were compromised. The DEA was not interested in putting me in touch with someone I could talk to this about. I reported this to the Richmond Virginia field office who were much more cooperative.
Method of Discovery:
This was discovered using a publicly accessible Google search with the query:site:dea.gov "roblox"
The search returned multiple suspicious entries from museum.dea.gov, leading to deeper inspection which confirmed pornographic and scam material being served directly from government-hosted pages.
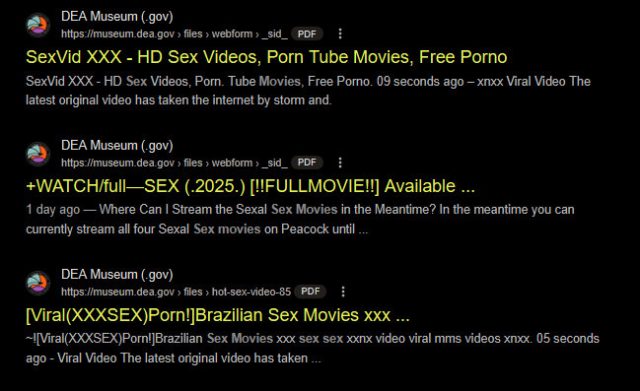
Examples of Affected URLs:
https://museum.dea.gov/files/webform/_sid_/robux-1-bxihttps://museum.dea.gov/_sid_/sex-stream-on-ushttps://museum.dea.gov/files/webform/_sid_/hot-sex-video-85https://museum.dea.gov/files/webform/_sid_/robux-13-p6-9https://museum.dea.gov/files/webform/_sid_/pro-13-e4-8https://museum.dea.gov/Sinners-streams-us1https://museum.dea.gov/hindi-filmyzilla-18
Technical Indicators:
- Directories involved:
/files/webform/,/_sid_/,/sites/default/files/ - PDFs with titles referring to pornography, pirated content, and scams
- Obfuscated filenames mixing Unicode, emoji, and special characters to evade filters
- Use of embedded links and downloadable “video” files masquerading as entertainment content
- Some URLs designed to attract children (e.g., Roblox Robux-related files)
Potential Vectors of Compromise:
- Vulnerabilities or misconfiguration in third-party form-handling plugins (e.g., Ninja Forms, Webform for Drupal)
- Insecure file upload configurations allowing unauthenticated or unsanitized content injection
- Poor access control on web directories used for form/file submission
- Absence of antivirus/malware scanning on uploads
- Possible lack of CAPTCHA or rate-limiting on form endpoints used to push files
Risks and Concerns (Including Ransomware Threat):
- Ransomware Entry Point: Uploaded files may contain scripts, droppers, or links to malicious payloads. If an administrator or user accesses or downloads these files from the
.govdomain believing them to be legitimate, this could trigger the execution of ransomware or other malware, encrypting files and demanding payment. - Public Trust Exploited:
.govdomains are widely trusted. Attackers are leveraging this to spread malicious or social engineering content, increasing the success rate of phishing, trojan deployment, or initial access to secure networks. - Malicious Pivoting: If the same server infrastructure is shared with internal DEA systems, attackers may exploit the web server as a pivot point for lateral movement within the government network.
- Persistent Access: Repeated uploads and use of form endpoints suggest that attackers may have created automated systems to maintain presence—a classic precursor to launching timed ransomware attacks.
- User-Level Compromise: Visitors who download these files may unknowingly install infostealers, keyloggers, or ransomware payloads, giving attackers credentials or access to broader networks (including government, corporate, or law enforcement systems).
- Legal and Operational Fallout: Hosting pornography and pirated media on a
.govdomain, particularly content targeting minors (via Roblox scams), could have legal consequences and deeply undermine credibility. It could also interrupt public-facing operations if mitigation requires taking the domain offline.
Recommended Actions:
- Quarantine all affected directories and remove public access immediately.
- Conduct a forensic review of all uploaded files, scripts, and access logs dating back to the first known appearance of unauthorized content.
- Audit all third-party plugins (e.g., Webform modules) and update or remove any with known vulnerabilities.
- Implement strict file upload controls: disallow executable formats, use MIME-type verification, and enforce strict file extensions.
- Scan all content using a sandboxed antivirus/malware scanner with ransomware behavior heuristics.
- Check for indicators of deeper compromise, including shell access, backdoors, or unusual admin behavior.
- Engage CISA and the FBI for federal incident handling and to assist in evaluating potential risk to other
.govsystems. - Notify internal stakeholders and cybersecurity response teams across the DEA.
- Temporarily disable the
museum.dea.govsubdomain if it cannot be safely isolated from broader infrastructure. - Communicate transparently with the public once the incident is contained, especially if any data exposure or malware risk occurred to visitors.


