Apprenticeship.GOV Website Compromised

Date:
June 27, 2025
Summary:
The Apprenticeship.gov website has been compromised. Numerous files and pages hosted under official .gov URLs now serve pirated movie advertisements, pornographic content, and scam PDFs related to Roblox’s Robux currency. These materials are being presented through improperly secured form submission or file upload endpoints (e.g., /webform/_sid_/, /files/). These compromised pages are now being indexed in Google Search, allowing global public access. The nature and volume of the content suggests a systemic vulnerability.
Method of Discovery:
The compromise was identified through open-source intelligence (OSINT) techniques using a Google query:
site:apprenticeship.gov "robux"
site:apprenticeship.gov "movies"
This revealed dozens of links to inappropriate or malicious PDFs hosted within the .gov domain. Inspection confirmed that the files contain scam and potentially malicious content that appears to be automatically uploaded.
About:
Apprenticeship.gov is an official U.S. government website operated by the U.S. Department of Labor (DOL). Its mission is to promote Registered Apprenticeship Programs (RAPs) that provide high-quality career pathways. The site helps employers and job seekers connect through apprenticeship programs and offers access to funding, technical assistance, and compliance tools. It plays a critical role in workforce development and public-private partnerships.
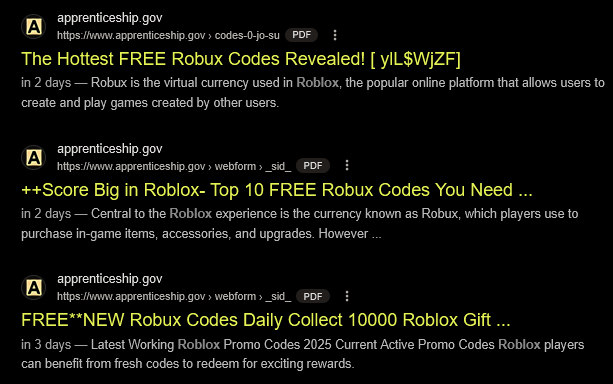
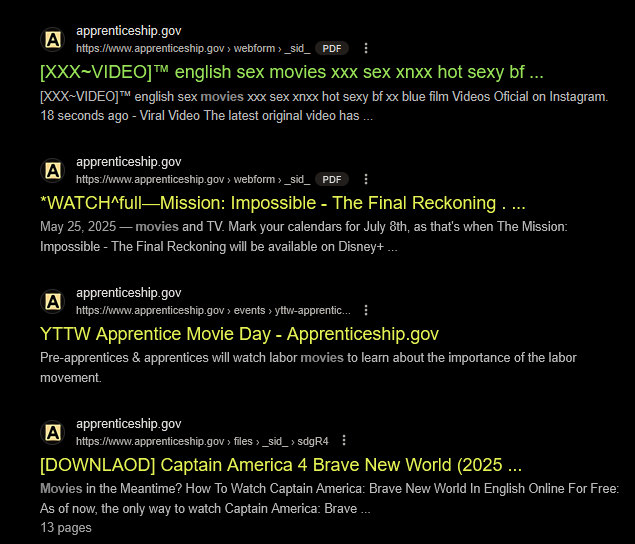
Examples of Affected URLs:
https://www.apprenticeship.gov/webform/_sid_/XXX-video-english-sexhttps://www.apprenticeship.gov/files/nRKuyLBR.pdfhttps://www.apprenticeship.gov/webform/_sid_/robux-codes-jo-suhttps://www.apprenticeship.gov/files/_sid_/sdgR4https://www.apprenticeship.gov/webform/_sid_/fullmovie-mission-impossiblehttps://www.apprenticeship.gov/webform/_sid_/roblox-free-generator-2j3MVhttps://www.apprenticeship.gov/webform/_sid_/kpop-demon-hunters-2025
Technical Indicators:
- Suspicious directories:
/webform/_sid_/,/files/,/codes-* - PDF documents with scam titles (e.g., “FREE Robux Codes,” “Captain America 4 Movie,” “XXX Sex Videos”)
- High frequency of newly created PDFs mimicking entertainment or gaming content
- Obfuscated file names and encoding tricks to bypass security filters
- SEO spam tactics used to get files indexed rapidly in search engines
Potential Vectors of Compromise:
- Unsecured file upload forms not properly sanitizing or validating input
- Third-party webform modules (Drupal Webform or similar) vulnerable to abuse
- Lack of CAPTCHA, rate-limiting, or access control for anonymous submissions
- Misconfigured access permissions on web directories
- Absence of automated malware and script scanning on uploaded files
Risks and Concerns (Including Ransomware Focus):
- Ransomware Payload Deployment
- Attackers could embed links or scripts in PDFs that lead to malware droppers.
- If a user (including site admins, job seekers, or partner orgs) downloads a poisoned file, it could trigger a ransomware infection that encrypts the local file system and demands payment.
- If accessed from a government or corporate workstation, this may escalate into a network-wide ransomware event.
- Trusted Domain Exploitation
.govdomains are highly trusted. Attackers can easily trick users into opening files or clicking links, dramatically increasing phishing and ransomware success rates.- Malicious actors often host loader scripts or redirectors on compromised trusted domains to evade email filters and antivirus defenses.
- Data Exfiltration and Privilege Escalation
- If these PDFs serve as initial access vectors, the attacker could gain a foothold and begin lateral movement across the network, looking for sensitive data or admin credentials.
- This is a common ransomware tactic, used to exfiltrate data before encryption, providing double extortion leverage.
- Botnet and Malware Distribution
- The current attack pattern suggests automation. It’s likely that bots are programmatically uploading scam PDFs, which may serve as loaders or stagers for malware kits, including ransomware-as-a-service (RaaS).
- These could be part of a campaign to build persistence on government networks before launching a coordinated ransomware attack.
- Reputation Damage and Legal Liability
- Hosting pirated, pornographic, or scam content on a federal
.govdomain, particularly content that targets minors (via Roblox scams), could lead to public relations disasters and Congressional scrutiny. - There are national security implications if attackers use the site to disseminate malware to other federal partners, contractors, or the public.
- Hosting pirated, pornographic, or scam content on a federal
Recommended Actions:
- Immediately quarantine and block access to the affected directories (
/webform/,/files/,/codes-*) - Perform a forensic analysis of all uploads since compromise, checking for embedded scripts, obfuscated payloads, or command-and-control links
- Audit all plugins, CMS modules, and forms—especially any custom or third-party form handlers
- Disable unauthenticated public upload features, or restrict them to vetted, logged-in users only
- Integrate antivirus/malware scanners into the file upload pipeline using services like ClamAV, OPSWAT, or VirusTotal API
- Notify CISA, US-CERT, and internal Department of Labor cybersecurity leadership
- Temporarily disable Apprenticeship.gov if the exploit cannot be safely contained
- Monitor outgoing traffic from this server to detect possible data exfiltration or botnet behavior
- Check for indicators of ransomware staging activity, including unusual outbound connections, file renames, or privilege escalation attempts
- Publish a notice or redirect for end-users warning them not to open suspicious PDFs and directing them to secure channels for apprenticeship content

